MSIX Digital Signing
Many of us are aware of the importance of securing our applications and how digital signatures are a solid way to avoid security breaches. For those looking into MSIX, you must know that Microsoft enforces digital signature for all packages within this technology. There is no exception.
In this article, we will go over the two main methods to digitally sign an MSIX package plus one additional method used for internal company apps.
What are the methods for digitally signing your MSIX package?
You can choose between a few options to comply with digitally signing your package as required by MSIX technology. Let's see how each of them work.

1. Signing MSIX packages when publishing to the Microsoft Store
Publishing your MSIX package to Microsoft Store is the easiest method as you don't have to manually set a digital signature. Instead, Microsoft takes care of that for you.
After you submit your application to the Store, Microsoft evaluates it and runs through the necessary steps: Security tests, Technical compliance tests, Content compliance.
Once these tests are passed, Microsoft automatically certifies your MSIX application and signs it.
2. Using a Certified Authority (CA) to Sign Your MSIX App
When it comes to using a certificate from a trusted CA (Certified Authority) to sign your MSIX application, you need to first acquire a certificate from a CA (such as Entrust Datacard, VeriSign/Symantec, DigiCert, Comodo, GoDaddy, and GlobalSign).
SHA256 hash algorithm is mandatory for digitally signing MSIX
packages, SHA1 is not considered as valid by the OS. So, make sure you
select the SHA256 algorithm when you order your certificate.
To sign the MSIX package, you need the Windows SDK where you will find the SignTool.exe, the command-line utility that Microsoft recommends for digital signatures.
You can download Windows SDK from here. Make sure to tick the “Windows SDK Signing Tools for Desktop App” option.
You can simplify your digital signing process even further by using Advanced Installer. With its SignTool integration and dedicated GUI, all you need to do is follow these steps:
- From the Product Information in the left pane, navigate to Digital Signature.
- There, you have to Enable Signing and select Use file from disk under Software Publisher Certificate. Then, simply browse your certificate file location.
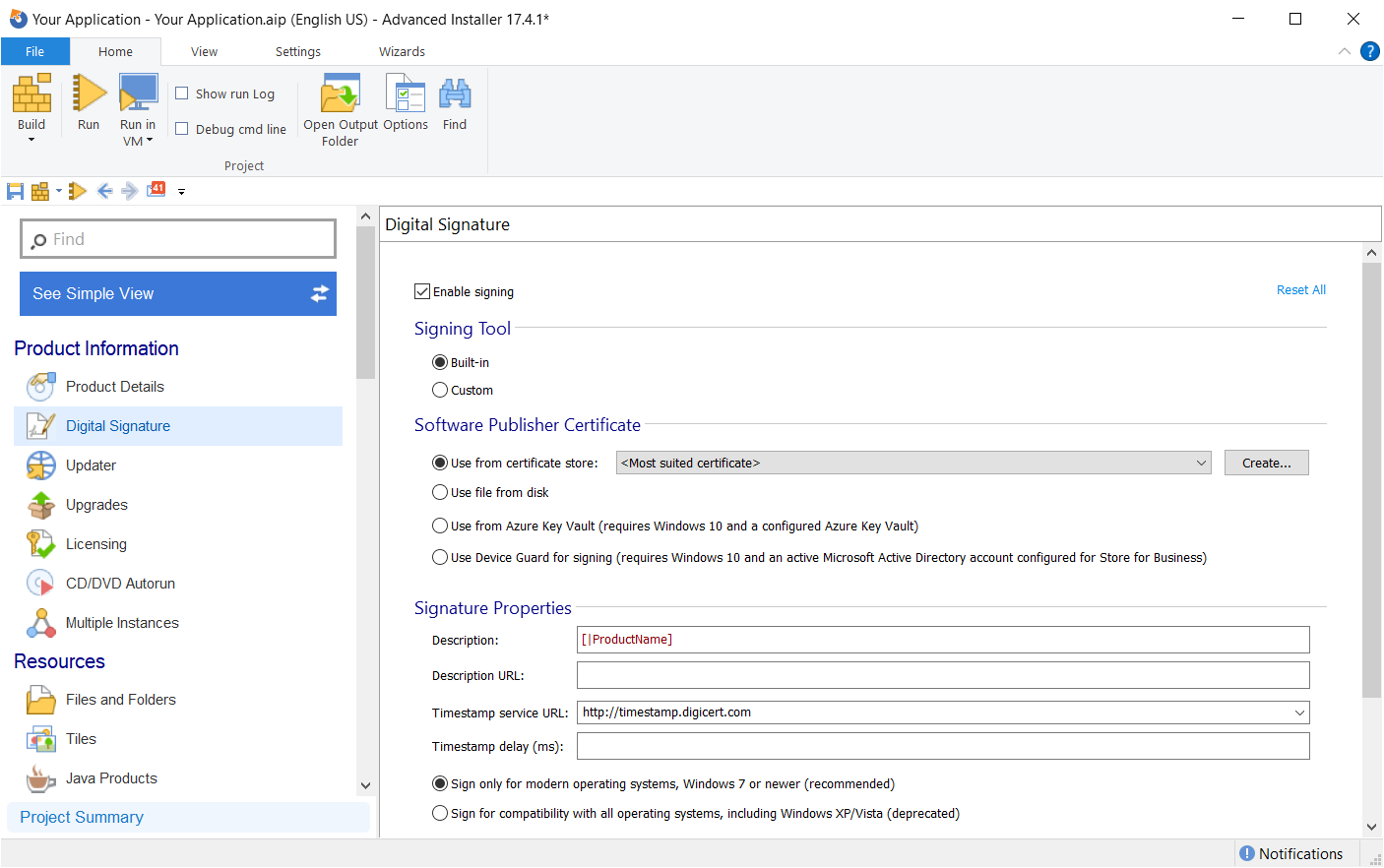
If you don’t have Advanced Installer, you can sign your package using with SignTool using the following command line :
SignTool sign /fd SHA256 /a /f signingCert.pfx /p password caphyonapp.msix
We recommend that you also timestamp your package to make sure your digital signature is
still valid even when your certificate expires.
If you want to time stamp the app package use the following command line:
SignTool sign /fd hashAlgorithm /a /f signingCert.pfx /p password /tr timestampServerUrl caphyonapp.msix
For additional information about SignTool, check out this link.
3. Generating an Internal Self-Signed Certificate
As we mentioned at the beginning of this article, for internal company apps or other tests, you can use a self-generated certificate to digitally sign your MSIX packages.
If you use this method, you should consider the following:
a) The certificate must be present on the targeted machine, where the package was deployed so the OS allows package installation.
This can be done by deploying the CA via group policy or any other preferred deployment method. Just make sure the certificate is stored under “Local Machine -> Trusted Root Certification Authorities” certificates store or manually install the certificate (by double clicking it) on the specific machine.
b) You have to enable Sideloading (starting with Windows 10, update 2003 this option will be enabled by default). To do that, follow the steps :
- Open the Settings app.
- Click on Update & security.
- Click on For developers.
- Under "Use developer features," select the Sideload apps option.
What are some ways to self-sign your application?
Now that we know the requirements for installing a self-signed application on a machine, let’s see some ways to self sign it.
3.1. Self-sign directly with Advanced Installer
From the same window that we used earlier to sign the package with a vendor certificate, we should now choose Use from Personal certificate store and click Create.
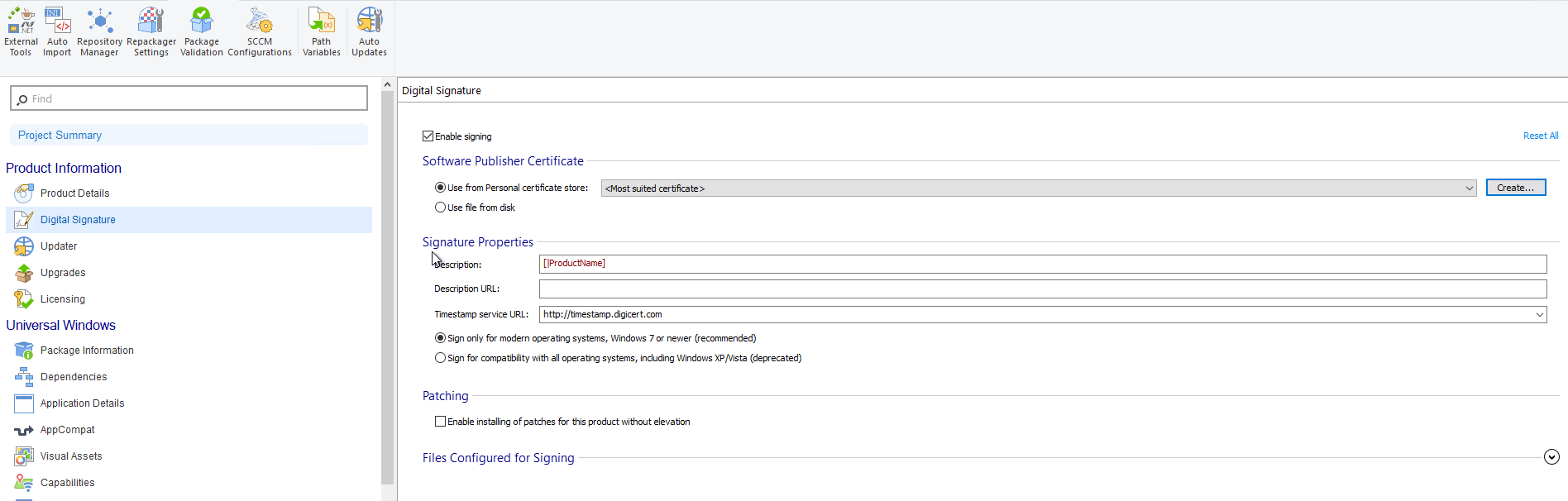
Advanced Installer uses CertMgr.exe for this operation. Make sure
you have it on the machine. CertMgr.exe is not available anymore as a
standalone download but it can be found in Windows SDK 7.
3.2. Sign using the SignTool command line
As mentioned above, if you don’t have Advanced Installer, you can sign your package using SignTool with the following command line:
SignTool sign /fd SHA256 /a /f signingCert.pfx /p password caphyonapp.msix
And then timestamp by following command line:
SignTool sign /fd hashAlgorithm /a /f signingCert.pfx /p password /tr timestampServerUrl caphyonapp.msix
3.3. Sign an MSIX package with Device Guard signing using Advanced Installer
Device Guard signing was introduced by Microsoft (starting with Windows 10 Insider Preview Build 18945) to protect users from malware threats. Device Guard signing is part of the Device Guard feature and can be found in the Microsoft Store for Business and Education.
Sign tools can interact with Device Guard signing to remotely sign packages specific to an Azure AD tenant. You can give a user signing permissions to have the ability of authenticating with their Azure AD identity and signing their packages.
For more details on how Device Guard instruction works, check out the official Microsoft release here.
Starting with version 17.3, Advanced Installer natively supports Device Guard signing for all your software packages(MSI, EXE, or MSIX).
To sign your packages, you can use the Advanced Installer's intuitive GUI or command lines. As mentioned above, it requires Windows 10 and an active Microsoft Active Directory account configured for Store for Business.
Learn more about the Device Guard signing feature in Advanced
Installer here
.
3.4. Sign an MSIX package with Azure Key Vault using Advanced Installer
With Advanced Installer's 17.4 update, you can sign your MSIX package using Azure Key Vault.
The Azure Key Vault integration ensures security and trust and enables you to properly manage and protect your code signing certificates.
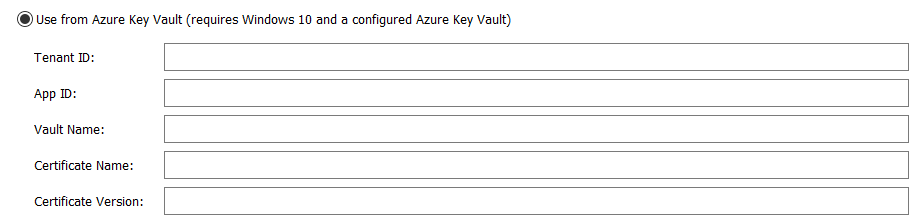
Keep in mind that Tenant ID, App ID, Vault Name, and Certificate Name are mandatory fields.
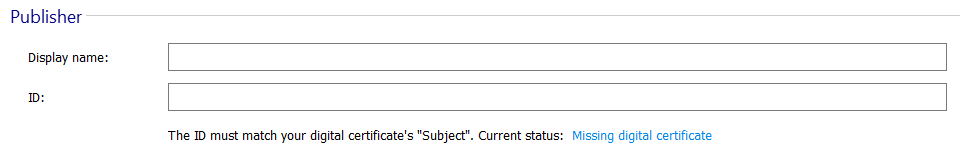
Also, make sure that the Published ID from the Universal Windows/Package Information pane matches your Digital Certificate subject.
Conclusion
As you've seen, there are various options to consider when signing your package depending on your particular needs and the nature of your MSIX application. I hope this article helps you in choosing the right method to sign your MSIX package application.
Also, we hope you try Advanced Installer's GUI!
We'd love to hear your feedback. What's your preferred digital signing method?
Subscribe to Our Newsletter
Sign up for free and be the first to receive the latest news, videos, exclusive How-Tos, and guides from Advanced Installer.